STOP/DJVU is one of the most widely spread ransomware that has reportedly affected thousands of victims all over the world. It spreads through keygens, cracked applications, fake application setup, fake Windows updates, and malicious email attachments. The ransomware encrypts the files, databases, and other data on the victim’s machine. STOP/DJVU ransomware attacks render SQL databases inaccessible. Losing access to the database and other files affects data availability and business continuity.
Here, we’ll be discussing a few mechanisms that you can use to recover the ransomware-affected files. Also, some preventive measures that can help you minimize or mitigate the impact of the DJVU ransomware.
What is STOP/DJVU Ransomware?
DJVU is a file-encrypting virus that belongs to one of the largest families of cryptovirus – STOP. STOP/DJVU ransomware attacks were first discovered in December 2018. Since then, the ransomware has been continuously changing its payloads and extensions to avoid detection, and has more than 290 versions. In addition to the United States, the ransomware has targeted victims from Asia, Europe, South America, and Africa. The DJVU virus uses Advanced Encryption Standard (AES) or RSA cryptography algorithm to encrypt files on victims’ machine, thus making the files inaccessible.
The victims can identify whether their system has been infected by DJVU ransomware by reading through the files extensions, like .djvu, .djvus, .udjvu, .uudjvu, etc.
How Does the STOP/DJVU Ransomware Work?
Once the victim's computer is infiltrated with the ransomware, it downloads the main executable file (tmp.exe) in the LocalAppData folder. In addition, the ransomware deploys several child files, including ‘updatewin.exe,’ ‘1.exe,’ ‘2.exe,’ and ‘3.exe.’
Find more about the executable files below:
- tmp.exe– It is the parent executable file.
- updatewin.exe– The encryption process begins when the ‘updatewin.exe’ file displays a fake Windows update dialog box.
- updatewin1.exe– It disables the functionalities of Windows Defender virus, such as the real-time scanning.
- updatewin2.exe– It changes the Windows hosts’ file, preventing the victim from requesting assistance from the security websites.
- updatewin3.exe– The functionality of this executable file remains unknown.
After deploying the executables, the DJVU virus encrypts the starting and end data of the database files, preventing access to them.
Once the encryption is complete, the ransomware drop notes (named ‘_openme.txt’ or ‘_readme.txt’) for ransom payment.
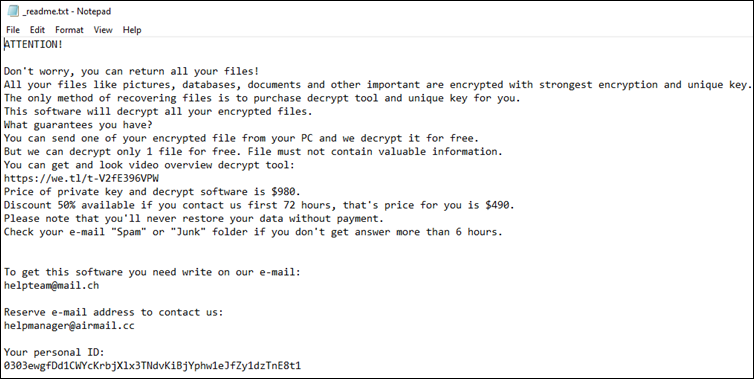
Note:Avoid paying any ransom to the DJVU’s developers, as several cases have cropped up wherein the victims could not access the files even after paying the ransom.
How to Recover SQL Databases Affected by STOP/DJVU Ransomware?
If your SQL databases are compromised due to malicious attacks, try to remove the ransomware using a malware removal tool. Subsequently, try to decrypt the database files or perform file recovery using the options discussed below. The detailed steps are as follows:
Step 1 – Use a Malware Removal Tool
下载恶意软件删除工具和性能可靠rm a thorough scan of the system to remove the DJVU virus from your system. Following are the basic steps you need to follow:
- Start your Windows PC in safe mode with networking.
- Download and install the malware removal tool.
- 关闭系统还原infiltrated components.
- Restart the Windows in safe mode.
- After restarting in safe mode, clean the Windows hosts file.
- Scan the computer using the malware removal tool to remove the virus.
- Once the virus is removed, start Windows normally.
Note:Using a malware removal tool does not guarantee the complete removal of the virus. Even if it is removed, some files might not get decrypted.
Step 2 – Recover the SQL Database Files
You can use backups to restore the database files. If the backups are not updated or corrupted, you can try to repair the database or extract backup data by using an advanced tool, like Stellar Toolkit for MS SQL. The toolkit comprises a powerful SQL database repair tool to fix corrupted database (.mdf/.ndf) files. Also, it has a backup extractor tool that helpsrecover data from corrupted .bak files.
If you want expert’s intervention in recovering data from ransomware-infected databases, you can seek the help of Stellar SQL File Repair and Recovery Services.
Preventive Measures to Protect SQL Databases from STOP DJVU Ransomware
Here are a few key recommendations to protect your system and SQL database from getting infected by ransomware:
1.Patch All the Things You Manage
It is obvious, but it's critical to keep systems up-to-date with the most recent Windows and SQL Server patches. While you can turn on automatic updates in Windows, check and install security updates for SQL Server released by Microsoft.
2.Things You Must Avoid
You can prevent your system from getting infected by following these practices:
- Do not install cracked software
- Do not click on links in suspicious mails
- Update antivirus program to keep your system protected against new ransomware variants
3.Perform a 3-Step Backup
One of the simple and effective methods you could implement to safeguard your database from the STOP DJVU ransomware is to do a 3-step backup. It means backing up all your important sensitive data following these steps:
- Back up all your database files in a separate partition within your system.
- Create another backup copy on an external storage media.
- Back up the files to secure cloud storage.
For further assistance to recover data from ransomware-infected files, leave a comment or contact our support team.













